Understanding the types of component risk
There are three types of risk being assessed for components used in projects:
Security Risk
Components are assigned one of four categories of security risk, based on the vulnerabilities associated with the versions in use in projects.
Vulnerabilities are linked to components by the CVE numbers, as reported in the National Vulnerabilities Database (NVD) maintained by NIST or by Black Duck Security Advisories (BDSA) numbers.
Note that the security risk values shown use CVSS v2 or CVSS v3.x scores, depending on which security risk calculation you selected; by default, CVSS v3.x scores are shown.
Possible risk categories are:
-
Critical. The component has critical high severity vulnerabilities.
-
High. The component has high severity vulnerabilities.
-
Medium. The component has medium severity vulnerabilities.
-
Low. The component has low severity vulnerabilities.
-
None. The component has no vulnerabilities.
License Risk
Projects are assigned one of four categories of overall license risk:
High. At least one version of the component in use in a project has a declared license that is high risk.
Medium. At least one version of the component in use in a project has a declared license that is medium risk.
Low. At least one version of the component in use in a project has a declared license that is low risk.
None. At least one version of the component in use in a project has a declared license that is no risk.
Click here for more information on how license risk for a component is determined.
Operational Risk
Operational risk is based on a combination of factors: (1) the strength of the component community, including the number of contributors and the level of commit activity; and (2) the number of newer versions of the component that are available, other than the one that is currently in use.
Project versions can have four categories of operational risk.
-
High. The component has high combined operational risk and a version is used in at least one project.
-
Medium. The component has medium combined operational risk and a version is used in at least one project.
-
Low. The component has low combined operational risk and a version is used in at least one project.
-
None. The component has no operational risk and a version is used in at least one project.
Additionally, if a component version's origin has been flagged with further Component
Intelligence risks, you can click the menu button found at the end of the
component's row ![]() and select Insights to view the component version's Insights page.
and select Insights to view the component version's Insights page.
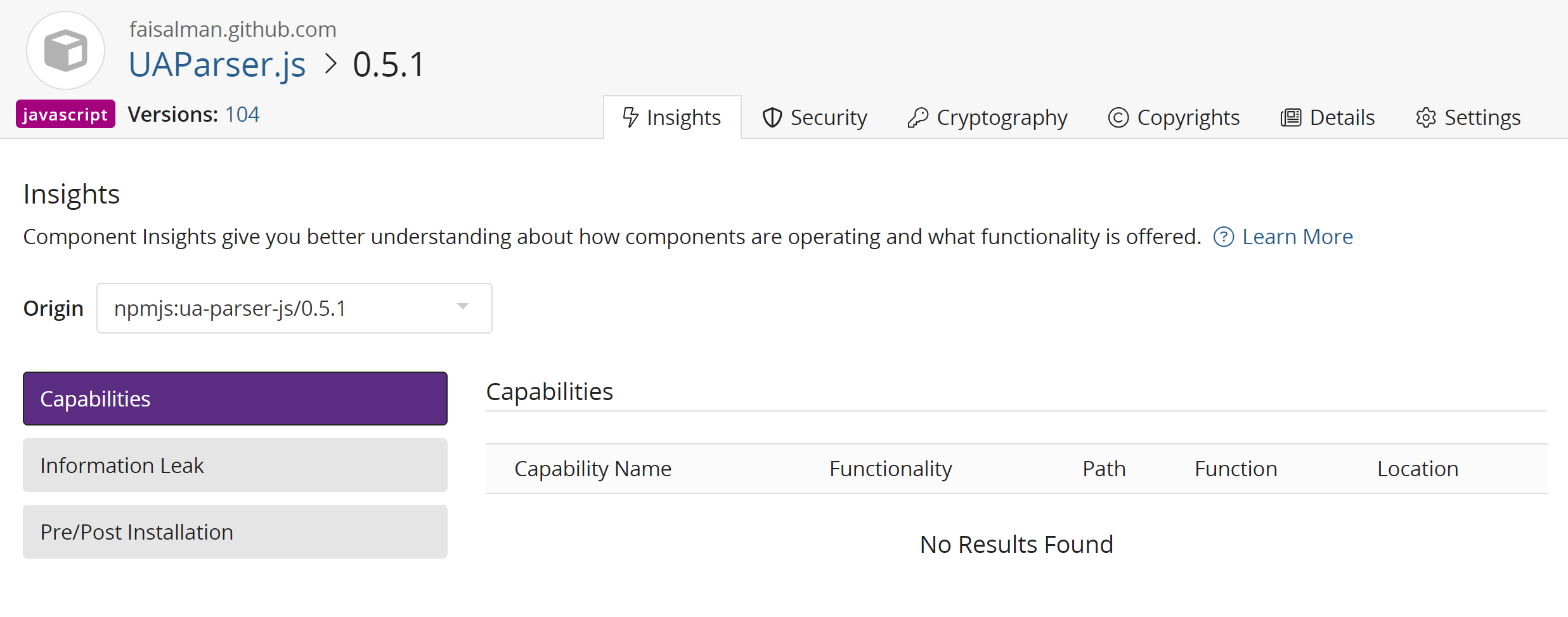
On this page, you can view a component version's insights:
Capabilities: Native functionality offered by the component. Capabilities currently detectable:
- Network Communications: The software component possesses the ability to communicate over the network.
- System Operation: The software component possesses the ability to execute system level commands.
- Cryptography: The software component possesses the ability to secure communications.
- Serialization: The software component possesses the ability to convert data structures to byte streams.
- File System Access: The software component possesses the ability to interact with the local file system.
- Compression: The software component possesses the ability to compress data.
- Security operations (Sanitizers & Validators): The software component possesses the ability to sanitize and/or validate input data.
Information Leak: Detected valid IPv4/6 addresses including domains identified within the codebase.
Pre/Post Installation: Various component configuration findings and observations. Observations may signify security and/or operational concerns.
