Analyzing the impact of a vulnerability
If a project version has several vulnerabilities, how can you decide which vulnerability you should focus on first?
To help you to prioritize which vulnerabilities you should address first, Black Duck can determine if any external public methods called by your Java applications are potentially involved in a known vulnerability. Black Duck can identify the called fully qualified public functional names in your source code and match them to the known function names being exploited by a vulnerability. By knowing whether any external public methods called by your Java applications are potentially involved in a known vulnerability, you can prioritize what vulnerabilities you need to concentrate on.
Vulnerability impact analysis works with Black Duck Security Advisories (BDSAs), a Black Duck-exclusive vulnerability data feed. Vulnerability metadata has been added to BDSAs that includes the fully qualified public function names that expose the vulnerability. Using this data, Black Duck can determine if vulnerable code is more likely to be invoked, and flags those vulnerabilities as reachable, indicating to you that these vulnerabilities are a higher priority for remediation.
Although Black Duck may indicate that a vulnerability is reachable, it does not indicate that the vulnerability definitely affects your code, as your code may not trigger the vulnerability.
Likewise, Black Duck may not denote that a vulnerability is reachable. However, that does not indicate that your code is safe from the vulnerability as Black Duck may not have data for a specific vulnerability.
Vulnerability impact analysis process
The process to display the possible impact of a vulnerability in Black Duck is:
1. Black Duck Detect analyzes the code
When the --detect.impact.analysis.enabled property in Black Duck Detect to set to true, Black Duck Detect creates a call graph (a list of calls made by your code) to understand the public methods your code is using in your application. The call graph shows the fully qualified public method names as well as the line number where the function was called.
Along with creating BOM files, Black Duck Detect creates a file which will be used by Black Duck KnowledgeBase for matching call graph signatures against BDSA-provided function signatures. This file is encrypted with SHA1 hashes. Hashing of the call graph signatures is completed at the client system.
The data is packaged into a single file and Black Duck Detect sends the file over HTTPS to the Black Duck server.
2. Black Duck sends data to the KnowledgeBase
Black Duck sends the hashed call graph function signatures to Black Duck KnowledgeBase via a Black Duck KnowledgeBase API.
3. Black Duck KnowledgeBase identifies vulnerable methods
The Black Duck KnowledgeBase uses the Function Signature Match Service to compare the hashed call graph signatures to KnowledgeBase hashed data for BDSA vulnerabilities with associated fully qualified public method names metadata. Fully qualified public method name matching is similar to signature matching: a discovered set of fully qualified public method names is compared against those known to the Black Duck KnowledgeBase.
The Black Duck KnowledgeBase sends the vulnerability metadata (vulnerable methods) to the Black Duck server via HTTPS.
4. Black Duck identifies vulnerabilities
Black Duck creates the data that needs to persist in the Black Duck PostgreSQL database. The data is stored as a new scan type (Vulnerability Impact) in Black Duck.
Black Duck cross references the identified methods with the vulnerable methods from BDSA to identify which vulnerabilities the user is calling in their code.
Black Duck displays the vulnerabilities for a component that have a method that is being called in the project version's Vulnerabilities tab.
Viewing reachable vulnerabilities
To view reachable vulnerabilities:
-
Set the --detect.impact.analysis.enabled property in Black Duck Detect to true to enable vulnerability impact analysis.
-
Once scanning completes and Black Duck has built the BOM, open the project version's Vulnerabilities tab which lists the security vulnerabilities for this project version.
-
Select a vulnerability from the table to view a table which lists the vulnerabilities for this component.
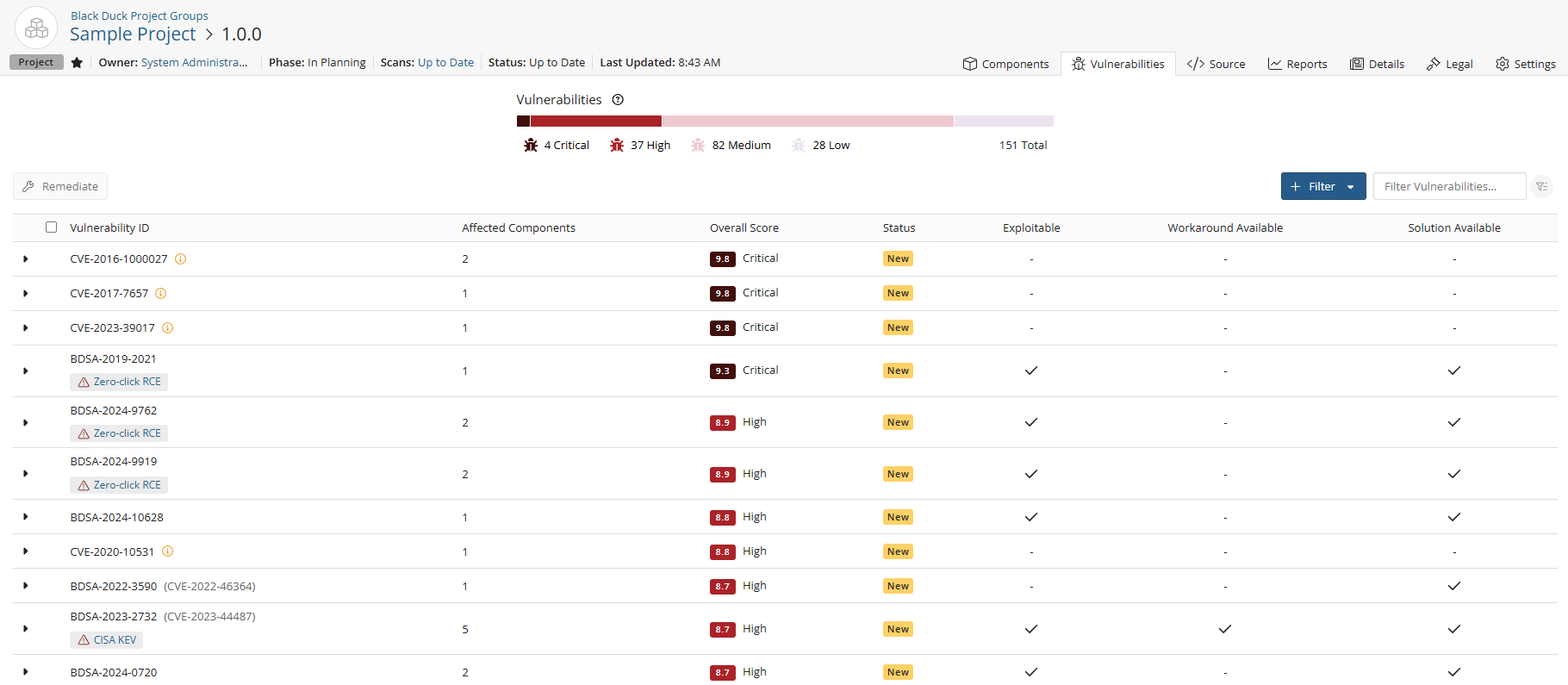
 located next to the BDSA record number indicates that there is a
function call in your code that makes this vulnerability reachable. Use the
Reachable filter to view all such BDSA records.
located next to the BDSA record number indicates that there is a
function call in your code that makes this vulnerability reachable. Use the
Reachable filter to view all such BDSA records.Click
 to view more information for an individual BDSA record.
to view more information for an individual BDSA record.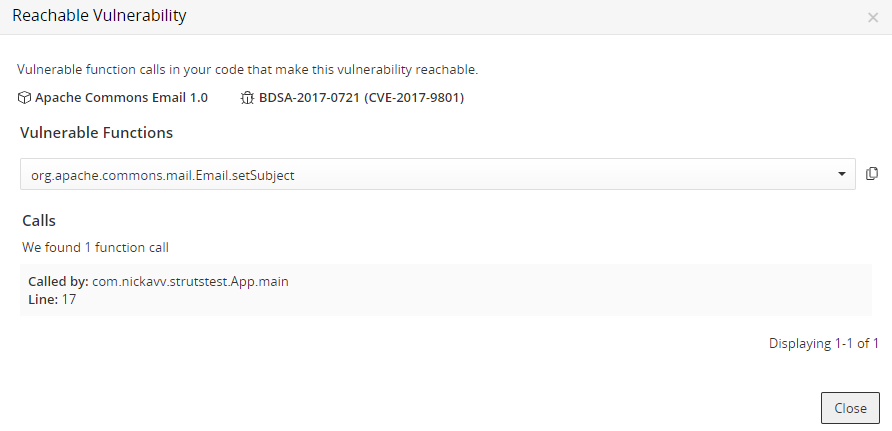
The Reachable Vulnerability dialog box lists:
-
Component name and version
-
BDSA record
-
A list of all vulnerable function calls in your code.
Select a function name to view the method name and line number in your code.
-
Note the following:
-
This feature is available in Black Duck Detect version 6.5 or later (and Black Duck Detect (Desktop) that uses Black Duck Detect 6.5 and later). Set the --detect.impact.analysis.enabled property in Black Duck Detect to true to enable vulnerability impact analysis.
-
This feature is for Java applications only. Black Duck Detect looks at Java
.classfiles only. -
Black Duck Detect only discovers vulnerabilities in public methods that call potentially vulnerable functions.
-
This feature displays reachable functions for BDSAs only.
-
There is a project version report,
vulnerability_matches_date_time.csv, that lists the component, vulnerability data, and vulnerability impact analysis data for each component potentially reached by a vulnerability. -
A vulnerability condition, Reachable from Source, is available enabling you to create policy rules for vulnerabilities which has been identified as reachable. Use this condition to create policy rules that prioritize those vulnerabilities.
