Viewing project version vulnerabilities
Use the project version page's Vulnerabilities tab to view the security vulnerabilities associated with the components used in a project version.
The information shown uses CVSS v3.x or CVSS v4.x scores, depending on which security risk calculation you selected; by default CVSS v3.x scores are shown.
This page has these sections:
-
Vulnerabilities graph
-
Filters
-
Vulnerabilities table
Vulnerabilities graph
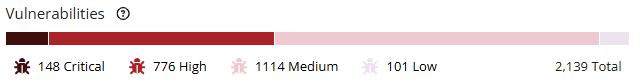
The Vulnerabilities graph shows how many vulnerabilities of each severity for each component version and subproject used in this version of the project.
This graph lists the number of components which have this level of security risk as their highest risk level – it is not the total number of components which have this risk level. For example, if you select to view components with a medium risk level, only those components that have medium as the highest risk level appear in the table; components that have both high and medium vulnerabilities are not shown.
Select a severity level in the Vulnerabilities graph to view all vulnerabilities that share the same level of risk.
Filters
Use the Filter components field to view specific components. Click  to view other available filters.
to view other available filters.
-
Some filter options apply to the values shown in the vulnerabilities table. If you select those filter options, components that have at least one vulnerability with the specified filter value will appear on the page.
-
Filters filter the list of components shown on the left side of the page. However, the data shown in the vulnerability table for those components is not filtered.
For example, if you select to view those components that have vulnerabilities with an overall score greater than 9.0, the page displays the list of components that have at least one vulnerability with an overall score greater than 9.0. The information shown in the vulnerability table for those components is not filtered: it still shows all vulnerabilities for the filtered components, including those vulnerabilities with an overall score less than 9.0.
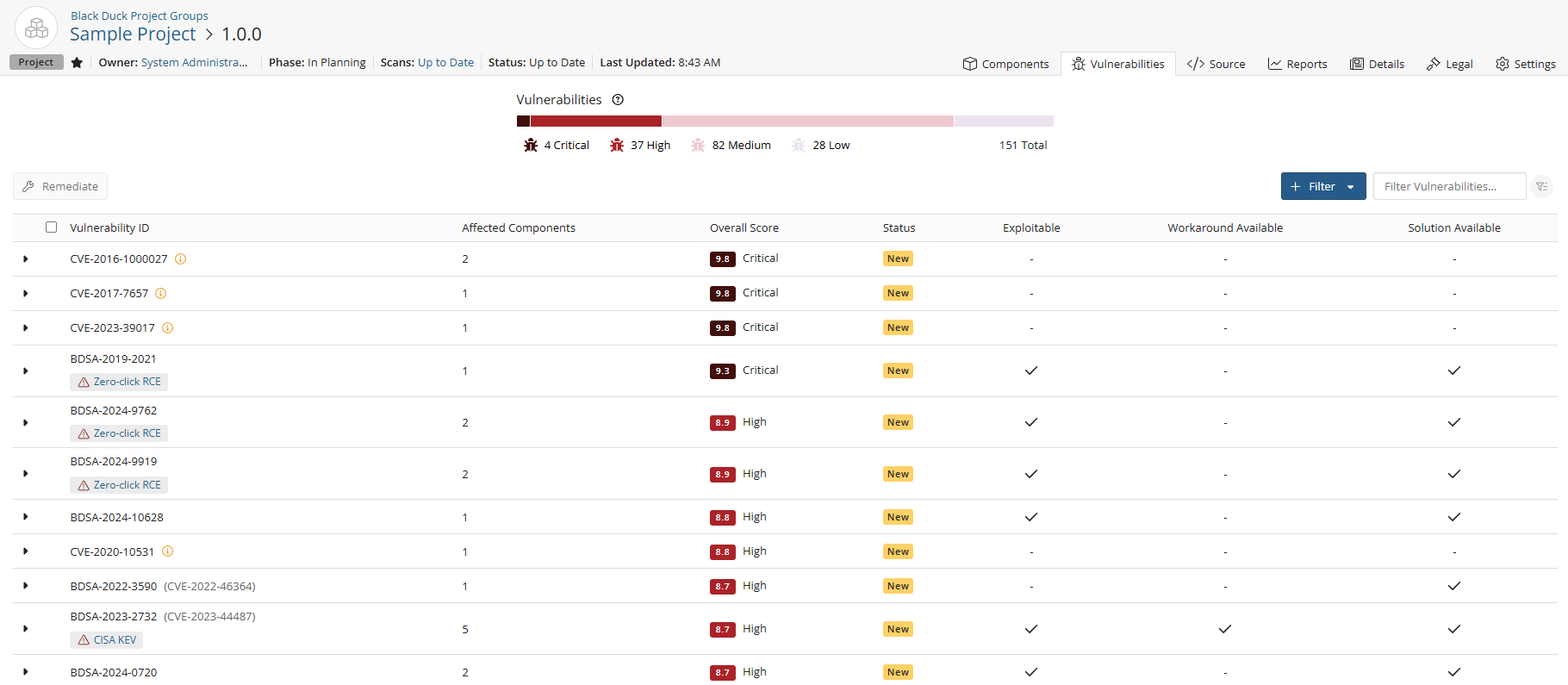
Vulnerabilities table
This section displays all vulnerabilities identified in the selected project version. For each entry, you'll see the vulnerability ID, the number of affected components, the overall risk score, current status, and indicators for exploitability, available workarounds, and available solutions.
Click ![]() next to a vulnerability to reveal additional
details.
next to a vulnerability to reveal additional
details.
The vulnerabilities table lists the following information for each vulnerability:
| Column | Description |
|---|---|
| Vulnerability ID |
The identifier, value associated with this vulnerability, and any vulnerability tags (if applicable). Select Users with the appropriate role can also use this section to remediate the vulnerability by clicking the |
| Affected Components | Displays the number of components in the project version affected by this specific vulnerability. |
| Overall Score |
Shows the Temporal score (for BDSA), or Base score (for NVD) and associated risk level. Hover over the Overall Score value to see the individual values.
The Temporal score represents time-dependent qualities of a vulnerability taking into account the confirmation of the technical details of a vulnerability, the existence of any patches or workarounds, and the availability of exploit code or techniques. The Base score reflects the overall basic characteristics of a vulnerability that are constant over time and user environments:
For more information, see the CVSS specification document section on Exploitablility Metrics. The Exploitability score measures how the vulnerability is accessed and if extra conditions are required to exploit it, taking into account access vector, complexity, and authentication. The Impact score reflects the possible impact of successfully exploiting the vulnerability, considering the integrity, availability, and confidentiality impacts. |
| Status | Remediation status of this vulnerability. Possible values are: Duplicate, Ignored, Needs Review, New, Mitigated, Patched, Remediation Complete, or Remediation Required. |
| Exploitable |
Indicates whether an exploit for this vulnerability is available:
|
| Workaround Available |
Indicates whether a workaround for this vulnerability is available:
|
| Solution Available |
Indicates whether a solution for this vulnerability is available:
|
