Black Duck Security Advisories
Black Duck Security Advisories (BDSAs) are a Black Duck-exclusive vulnerability data feed sourced and curated by our Cybersecurity Research Center (CyRC). BDSAs offer deeper coverage for a wide set of vulnerabilities than is available through the National Vulnerability Database (NVD). While providing more timely and detailed vulnerability insights, including severity, impact and exploitability metrics. BDSAs also provide actionable remediation guidance to save time by providing details on fixed versions, patch information, exploits, and workarounds where available. Validated additional vulnerability references are also provided under the Technical page on BDSA records.
The CyRC team provide detailed vulnerability guidance over beyond what the NVD typically provide in CVE records. BDSA are also cross-checked and validated against possibly affected component versions this often results in additional and more accurate mappings for components and versions affected by a given vulnerability.
Where a BDSA has not been mapped to a component version which is mapped to a CVE record this indicates that the COSRI's team additional research has determined that this component version is not affected by the vulnerability. BDSAs are frequently reviewed and updated often on an hourly basis in the event of a new zero day vulnerability.
The NVD CVE records are typically not cross-checked nor does the NVD verify vulnerability data published or provided from 3rd parties. The NVD are typically slower to update their records when new vulnerabilities or data becomes available.
BDSA records should not be considered separate vulnerabilities from CVE records or other publicly available vulnerability data sources but instead viewed as additional research and insights which users can use to make better decisions, faster with regard to open source security vulnerabilities.
Viewing a BDSA record
To view a BDSA record:
-
Use the Search feature to locate BDSAs.
For example, search for BDSA-2017 to see the list of Black Duck Security Advisories from 2017.
Select a BDSA to view the record.
-
Use the Security tab for a project version to view the vulnerabilities for a project version BOM.
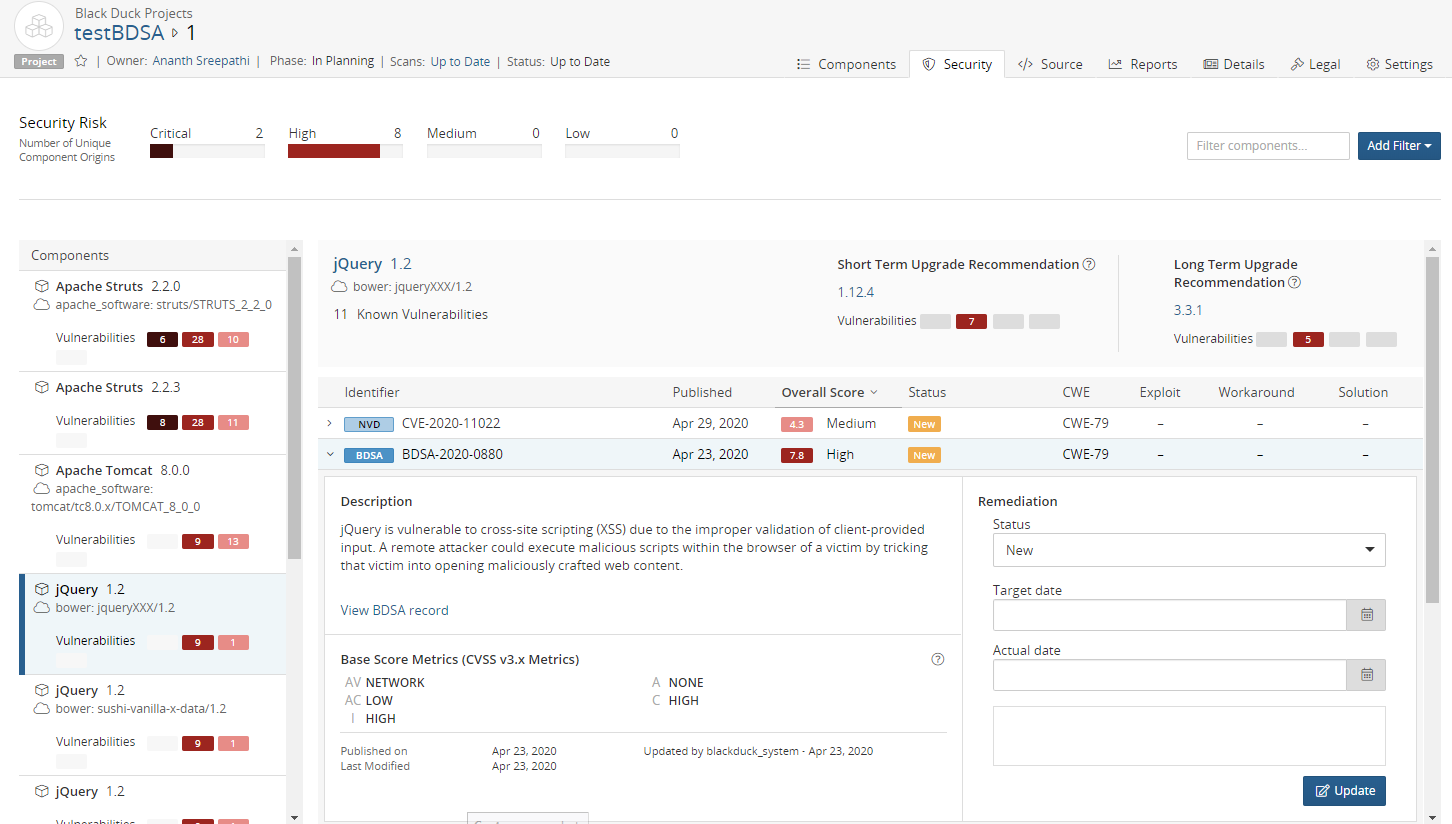
The BDSA identifier (
 ) indicates those vulnerabilities with a BDSA record.
) indicates those vulnerabilities with a BDSA record.Click > to view a description of the vulnerability and select View BDSA record.
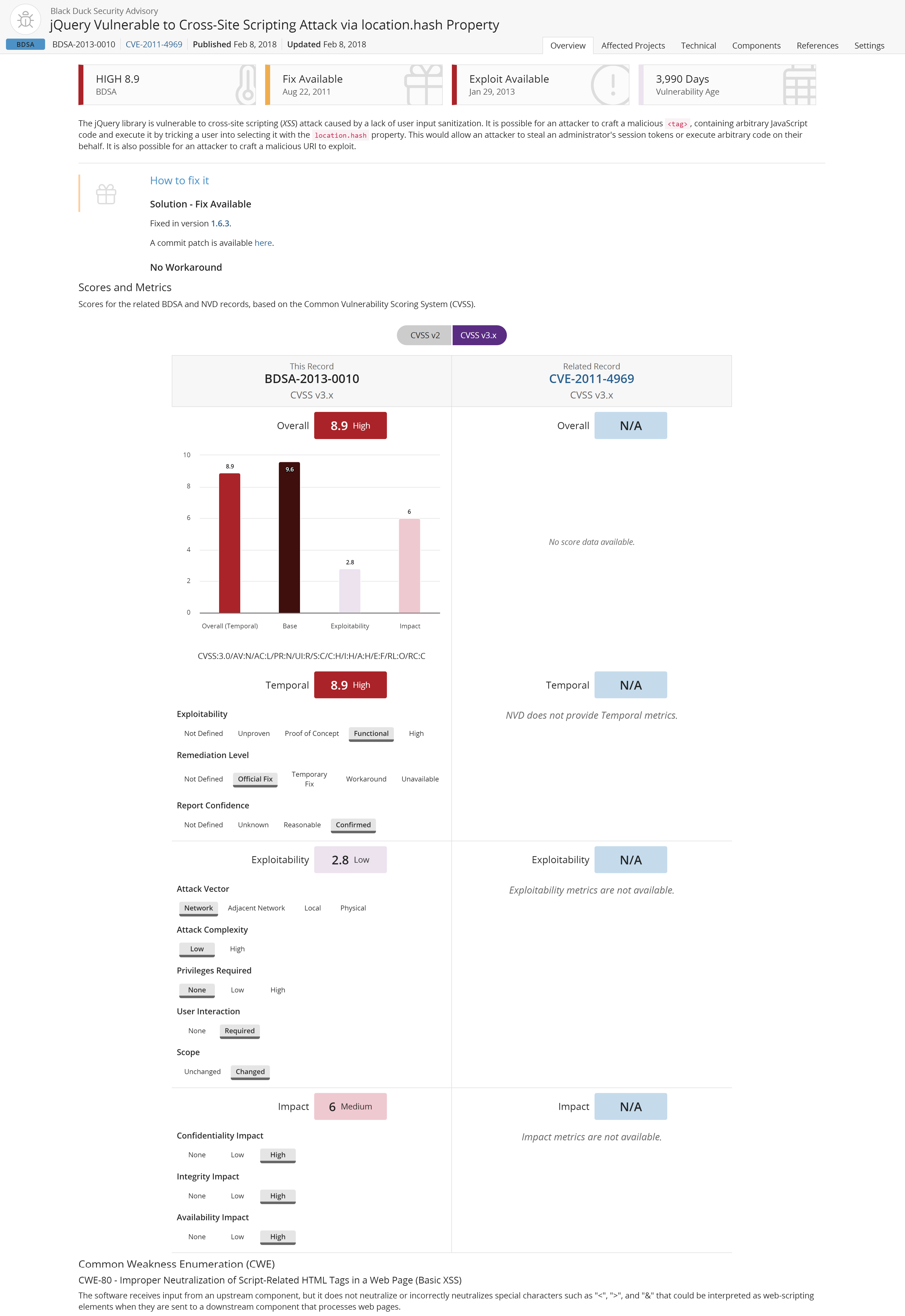
Overview tab
By default, the Overview tab appears and displays the following information:
-
The title bar displays the name of the vulnerability, BDSA number, CVE number (if there is a related CVE vulnerability), a published date (also known as the disclosure date), and an updated date (the last time the record was updated by NVD or BDSA).
-
At the top of the page, the following information appears:
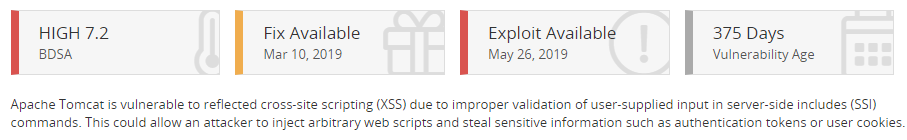
Shown here are the:
-
BDSA score. Score based on analysis by Black Duck Software security analysts, who further investigated the vulnerability and provided a more detailed and accurate score. This includes the temporal score.
-
Date of an available fix (if there is a fix available).
-
Whether there is an exploit for this vulnerability.
-
Vulnerability Age. Today's date - Disclosure date.
-
A brief description of the vulnerability.
-
-
The Vulnerability Tags section displays any specific vulnerabilities for this particular record, if applicable:
- Zero-click Remote Code Execution (RCE). This vulnerability can result in the execution of
code on the system, triggered by a remote attacker without requiring or
relying on any third party action.
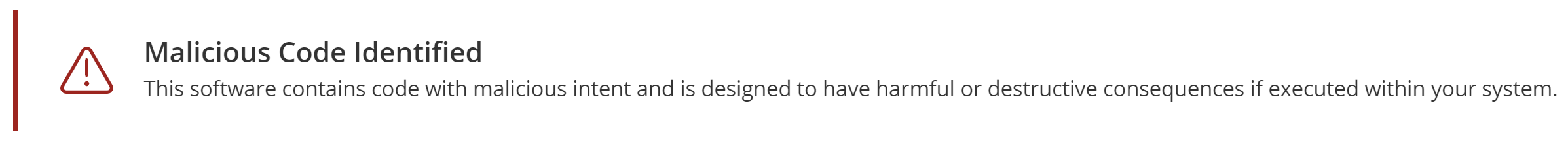
- Malicious Code Identified. This software contains code with malicious intent and is
designed to have harmful or destructive consequences if executed within
your system.
- Embargoed Vulnerability Details. Technical details of this vulnerability are currently
under embargo and the details are not published by the vendor at this
time. An embargo remains in place for a fixed period. The BDSA record
will be reviewed and updated with further details where possible once
the embargo has been lifted.
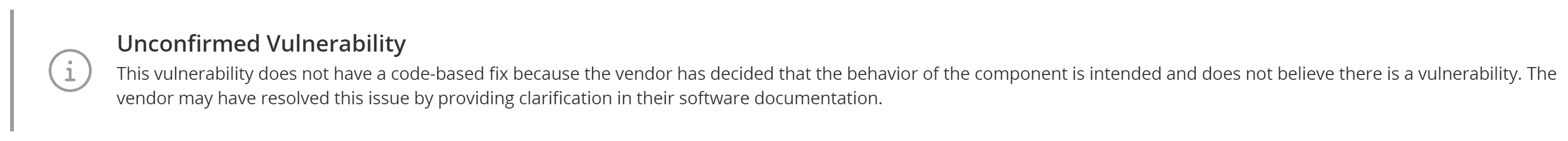
- Uncomfirmed Vulnerability. This vulnerability does not have a code-based fix because the
vendor has decided that the behavior of the component is intended and
does not believe there is a vulnerability. The vendor may have resolved
this issue by providing clarification in their documentation.
-
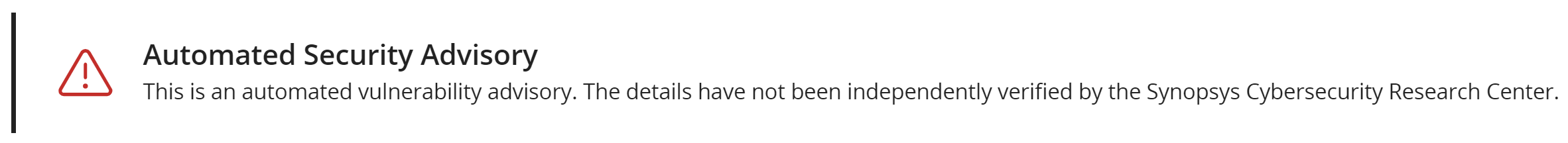
Automated Security Advisory (ASA). Automated Security Advisories are automatically created by Black Duck's Cyber Security Research Center using automated AI tools. ASAs are created from various trusted security feeds such as the GitHub Security Advisories (GHSA) feeds along with automated vetting using AI tooling. These advisories are designed to supplement the BDSAs identified and verified by our Cyber Security Research Center.
-
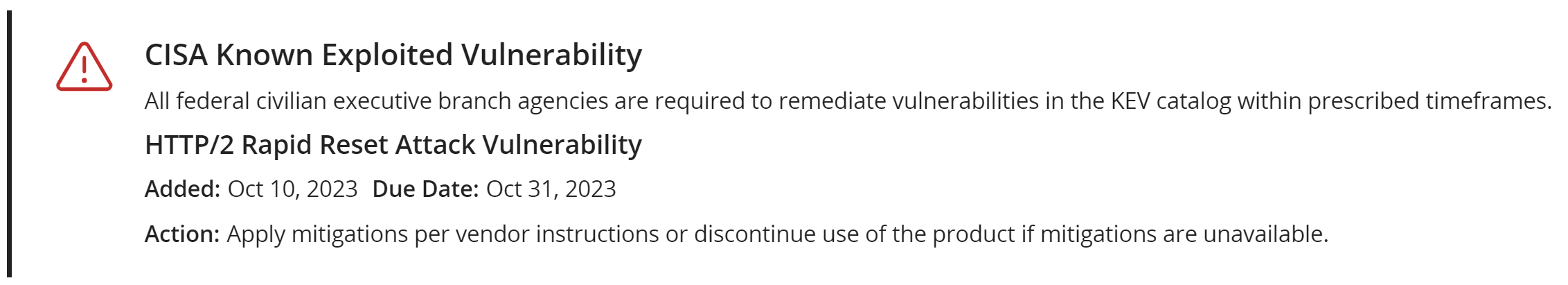
CISA Known Exploited Vulnerability. This vulnerability is listed in the Cybersecurity & Infrastructure Secrity Agency's (CISA) catalog. All federal civilian executive branch agencies are required to remediate vulnerabilities in the KEV catalog within prescribed timeframes. Please visit CISA's Known Exploited Vulnerability Catalog page for more information.
-
AI Assisted. AI Assisted Security Advisories are automatically created by the Black Duck Cybersecurity Research Center using automated AI tools. These BDSAs have not been independently verified by the BDSA team but are created using automated processes and generative AI assistance. These advisories are designed to supplement the BDSAs identified and verified by the Cybersecurity Research Center.
- Zero-click Remote Code Execution (RCE). This vulnerability can result in the execution of
code on the system, triggered by a remote attacker without requiring or
relying on any third party action.
-
The How to fix it section describes a solution, if one is available, and a workaround.
-
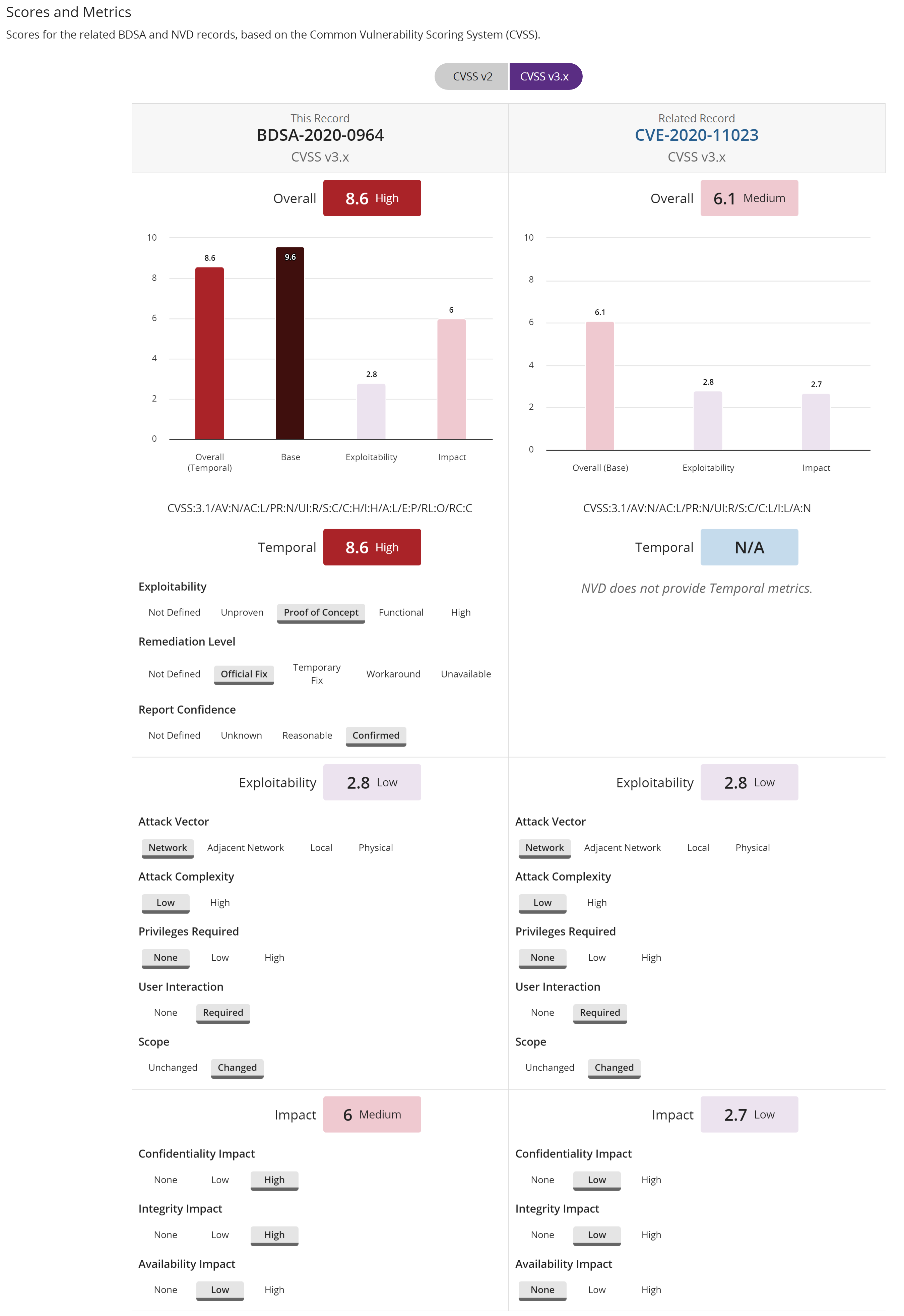
The Scores and Metrics section displays the scores for the related BDSA and NVD records (if applicable), based on the Common Vulnerability Scoring System (CVSS). Select a value above the graph to view the information in the graph and details below.
This section may also display a comparative, side-by-side graph if the vulnerability also has a NVD record.
Affected Projects tab
Select this tab to see a list of your projects that are affected by this vulnerability.
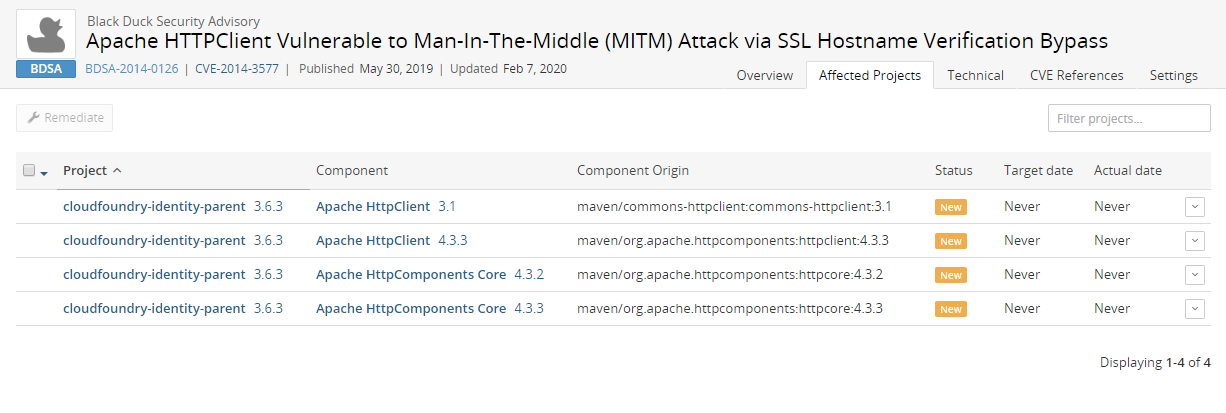
This tab lists all projects affected by this vulnerability:
-
Project name and version affected by this vulnerability.
-
Component name and version that contains this vulnerability.
-
Component origin that contains this vulnerability.
-
Remediation status of this vulnerability. Possible values are: New, Needs review, Mitigated, Patched, Duplicate, Remediation Required, Remediation Complete, or Ignored.
-
Target date for remediating this vulnerability.
-
Actual date this vulnerability was remediated.
Select ![]() in the row of a
project and select:
in the row of a
project and select:
-
View all vulnerabilities to view all vulnerabilities affecting this project version.
-
View related files to view to display the Source tab filtered to display the affected files.
Use this tab to remediate the vulnerability for one or more projects by origin:
- In the row of the single project you want to remediate, do one of the following:
Select
 , select Update Remediation Plan, enter the
remediation details, and click Update.
, select Update Remediation Plan, enter the
remediation details, and click Update.Select
 and click Remediate. Enter the remediation details,
and click Update.
and click Remediate. Enter the remediation details,
and click Update.
-
For multiple projects that need the same remediation status, select
 in each row and click Remediate. In the Bulk Remediation
dialog box, enter the remediation details, and click Update
in each row and click Remediate. In the Bulk Remediation
dialog box, enter the remediation details, and click Update
Technical tab
Select the Technical tab to view a technical description and a list of references and related links.
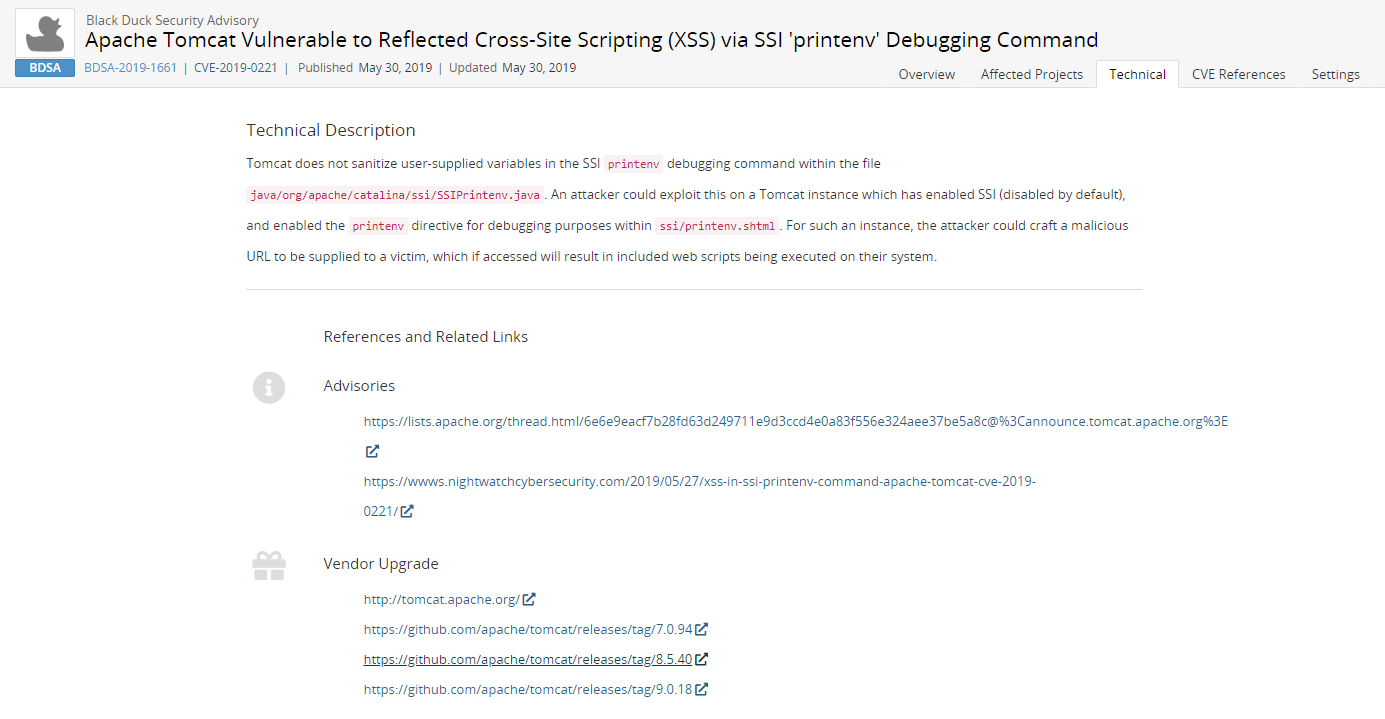
Included in the References and Related Links section is a list of Key Events:
-
Discovered. Date that the vulnerability was discovered.
-
Vendor Notified. Date the official vendor was notified of this vulnerability.
-
Vendor Fix. Date that the official vendor released a patch or upgrade to fix this vulnerability.
-
Disclosure. Date the vulnerability was first publicly disclosed, whether as a bug or as a security vulnerability.
-
Vulnerability Age. Today's date - Disclosure date.
-
Exploit Available. Date an exploit became publicly available for this vulnerability.
Components tab
Select the Components tab to view a list of all known component versions affected by this particular BDSA vulnerability record.
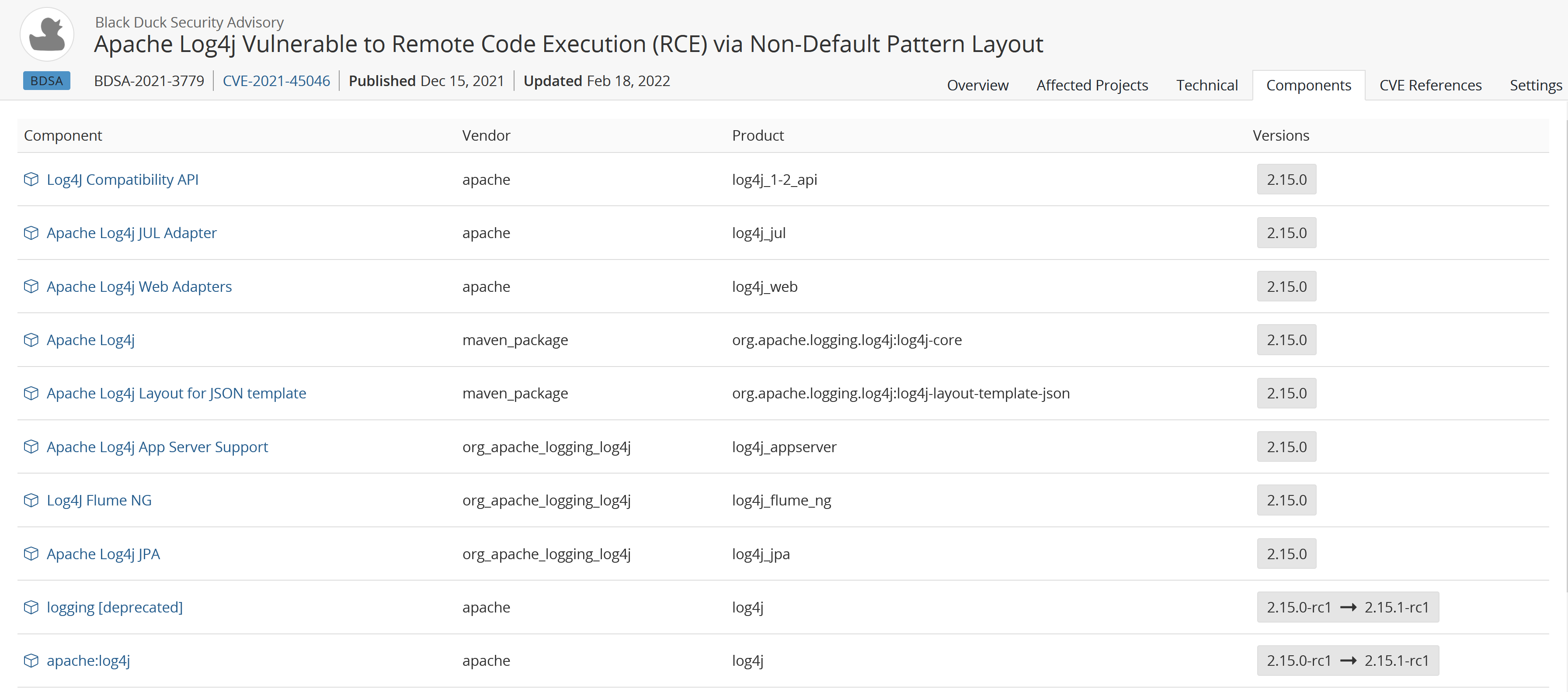
CVE References tab
Select the CVE References tab to view links for additional information.
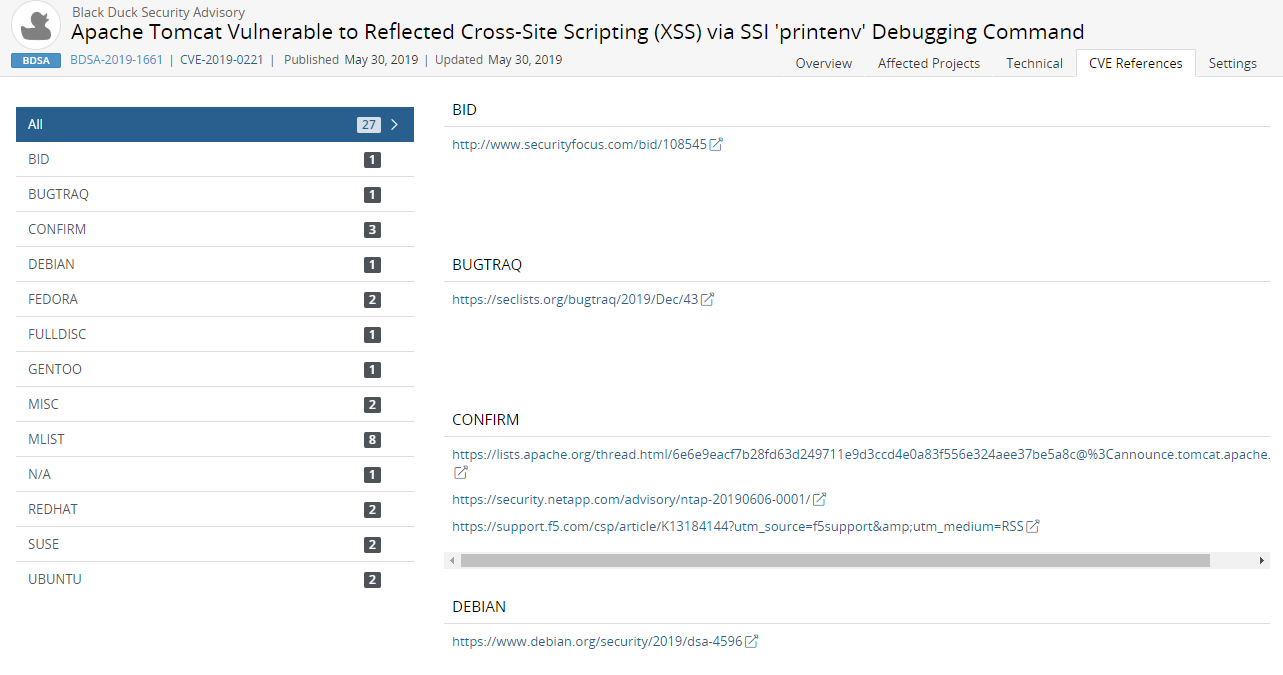
Settings tab
Use this tab to manage the global remediation for this vulnerability. Click here for more information.